This topic is relevant to security gateways and managed switches. You are viewing the version of this content for security gateways.
Click here to view the version of this content for managed switches.
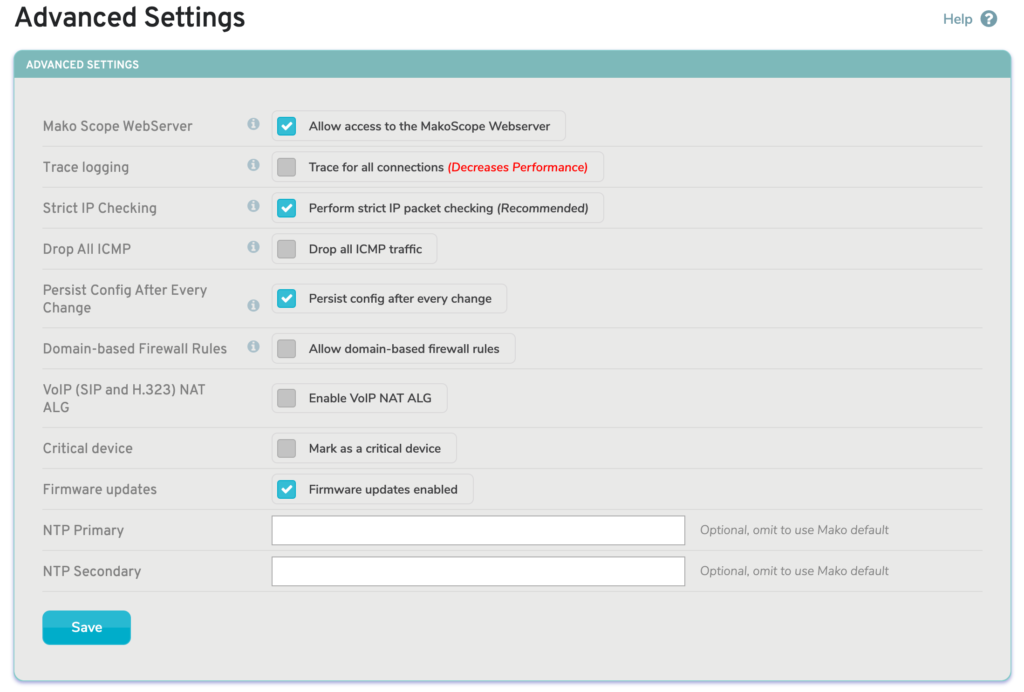
Figure 1. Advanced Settings Page
The Advanced Settings page (Fig. 1) in the Services menu of the Configure section of the Central Management System (CMS) allows you to manage advanced settings related to services running on the selected Mako.
MakoScope WebServer
The MakoScope WebServer setting is enabled by default. This feature displays basic diagnostic and operating information for your Mako when you type its LAN IP address or http://1.2.3.4 into a web browser. This information is only viewable if the web browsing device is also connected to the LAN.
This is a global setting that affects all networks on the selected Mako, however each LAN also has its own MakoScope WebServer setting available on the LAN page.
Trace Logging
The Trace Logging setting is disabled by default. Trace logging allows you to trace all connections allowed and denied through the firewall. The trace information can be viewed on the Reports >> Syslogs page by selecting the “Firewall Logs” type. Trace logging all connections will negatively impact performance and should only be enabled while troubleshooting firewall-related connection problems. Trace logging is disabled automatically after four days.
This is a global setting that affects all firewall rules on the selected Mako, however each firewall rule has its own Trace Logging setting available. See the Firewall documentation for details.
Strict IP Checking
The Strict IP Checking setting is enabled by default. Strict IP checking ensures that all IP packets passing through the firewall are not malformed or invalid. Disabling this will relax some of the checking performed, but not all of it. Some applications are known to only work when this is disabled. Disabling Strict IP Checking is not recommended.
Drop All ICMP
The Drop All ICMP setting is disabled by default. Enabling this will drop all Internet Control Message Protocol (ICMP) traffic passing through the selected Mako. Blocking ICMP traffic is done to prevent ICMP replay attacks. One side effect of this is that tools like ping and traceroute will no longer work.
This is a global setting that affects all ICMP traffic on the selected Mako, however each network has a similar Allow Ping setting available that can affect ICMP traffic. See the Internet and Network documentation for details.
Persist Config After Every Change
The Mako device has a config file in persistent storage that is referenced during booting, prior to connecting to the CMS.
The Persist Config After Every Change setting is disabled by default. When disabled, only critical changes, such as WAN settings changes, result in an updated persistent config file; all other changes are implemented after the Mako connects to the CMS.
When enabled, all changes, no matter how small, result in an updated persistent config file. There is a delay of approximately 30 minutes between making changes in the CMS and the persistent config file being updated. This allows time to roll back any problematic changes in the CMS and reboot the Mako with the working persistent config file before it gets updated.
Domain-based Firewall Rules
The Domain-based Firewall Rules setting is disabled by default. Enable this to allow domain-based outbound firewall rules to be created on the selected Mako. When enabling this, you will be asked to accept a warning message explaining how this functionality works.
Domain-based firewall rules match the domain and all subdomains, e.g. “example.com” will match both example.com and www.example.com. The rule will also match all IP addresses that resolve to the specified domain and its subdomains.
Domain-based firewall rules require that clients use the Mako’s built-in DNS service. You can force all clients on a LAN to use the Mako’s DNS service by enabling the DNS Intercept option for the LAN.
WARNING: Domain-based firewall rules should only be used where the DNS server is secured from tampering, otherwise there is a risk of an intercepted DNS query providing the wrong IP information for the domain, resulting in the firewall rule allowing access to an unintended destination.
VoIP (SIP and H.323) NAT ALG
The VoIP (SIP and H.323) NAT ALG setting is disabled by default. Enable this to activate VoIP firewall helpers that may resolve issues in certain cases when VoIP clients and/or servers are behind NAT.
Critical Device
The Critical Device setting is disabled by default. Enable this to mark the selected Mako as a critical device. When enabled, you will be asked to confirm any configuration changes, which should help to prevent accidental changes that could have serious consequences.
Firmware Updates
The Firmware Updates setting is enabled by default. The selected Mako will automatically update its internal software periodically, unless you choose to disable this setting.
Save Button
To save any changes to these settings, click the “Save” button.
