Overview
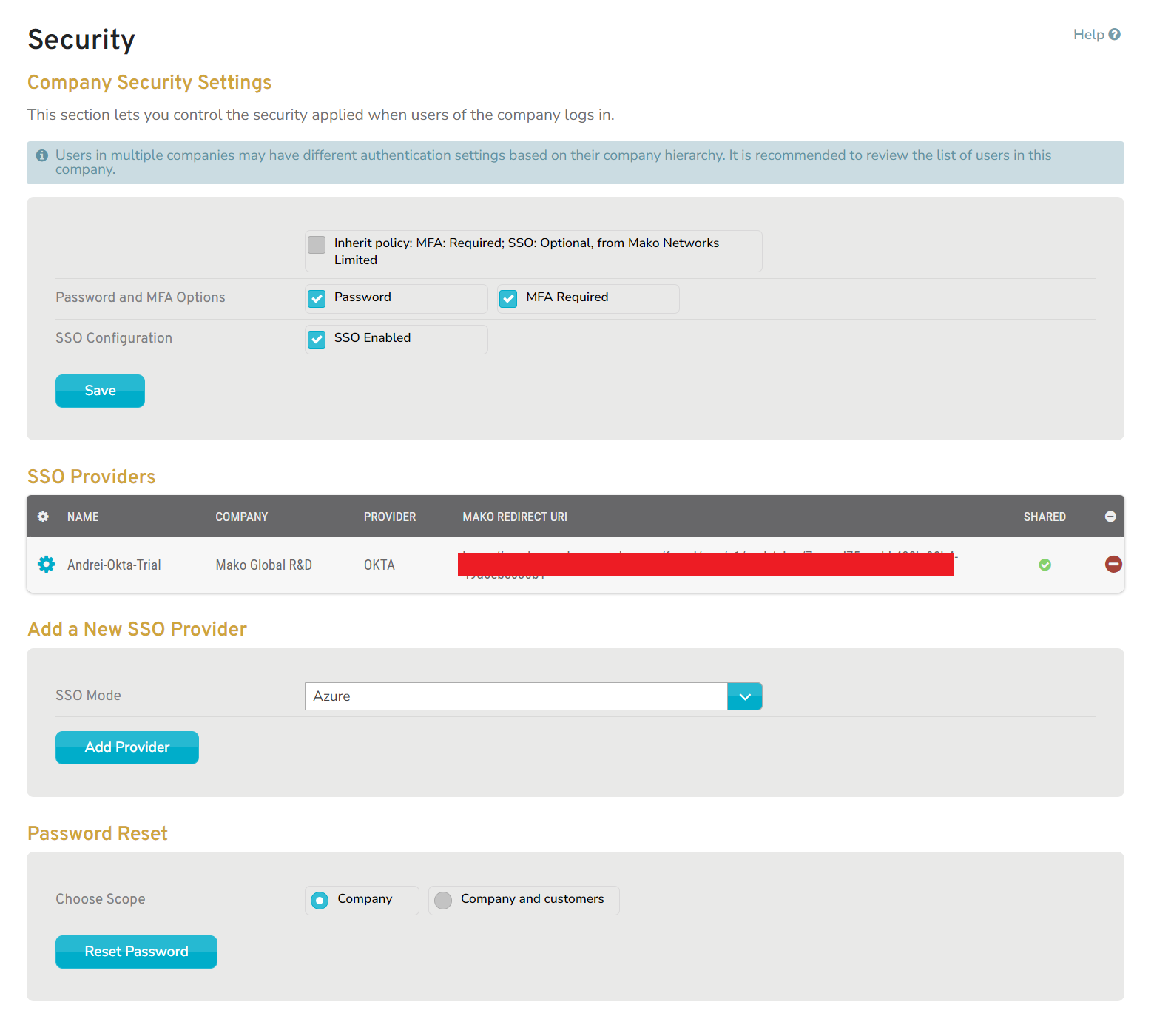
Figure 1. Example Company Security Page
The Company Security page (Fig. 1) allows you to manage login security options for users of the selected company and to reset their passwords in bulk.
Single Sign-On
Single Sign-On (SSO) allows certain users to access the Mako CMS using an existing third-party account created for another system via an SSO identity provider (IdP). The company security settings determine which providers, such as Microsoft or Okta, are available to the company’s users, if any.
For Mako CMS accounts without SSO, account credentials are managed via the Mako CMS. For Mako CMS accounts with SSO, account credentials are managed via the SSO identity provider.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) adds an extra layer of security to user accounts by requesting a new access code each time the user logs in. MFA is recommended for any user, but it is required for those maintaining PCI DSS compliance.
Companies that require PCI DSS compliance must enforce MFA for all users. For Mako CMS accounts without SSO, MFA is managed via the Mako CMS. For Mako CMS accounts with SSO, MFA is managed via the SSO identity provider.
Company Security Settings
Company Security Settings Form
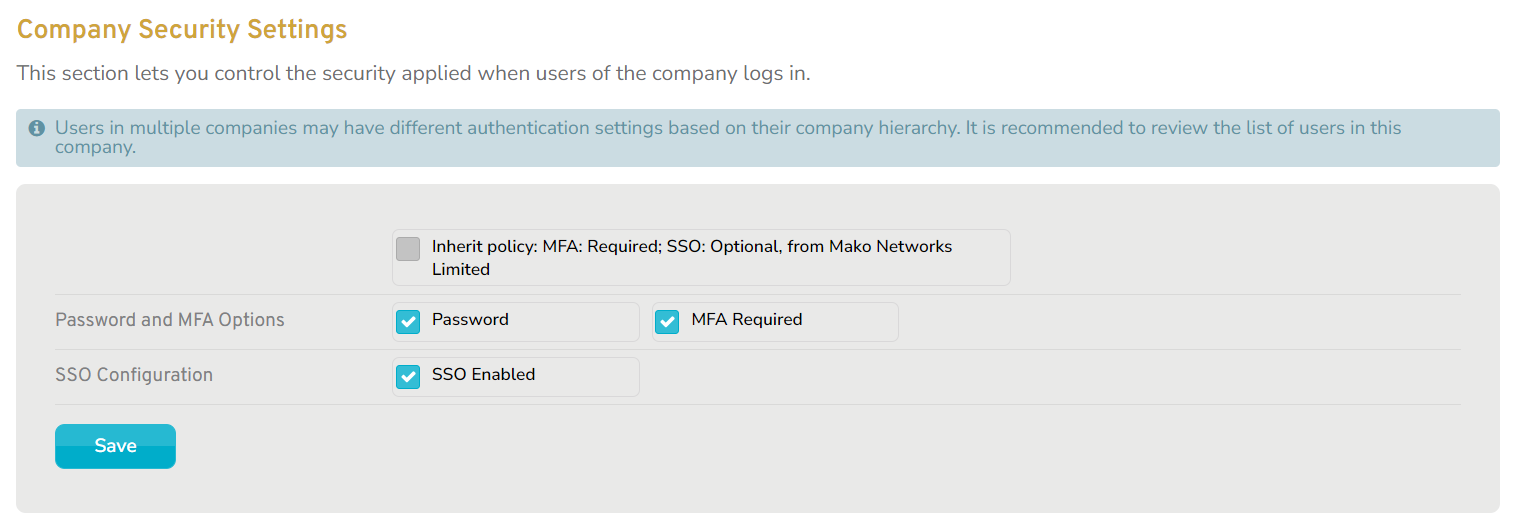
Figure 2. Example Company Security Settings Form
The Company Security Settings form (Fig. 2) allows you to manage login security options for users of the selected company.
Users in multiple companies may have different authentication settings based on their company hierarchy. It is recommended to review the list of users in this company before making any changes to these settings.
Form Fields
Inherit Policy
If the selected company has a parent company, choose whether or not the company security settings should be inherited from the parent company.
A summary of the parent company’s settings is displayed to help you choose.
The default behavior for a new organization in the Mako CMS is as follows.
- Password accounts are enabled with MFA optional.
- SSO accounts are enabled.
The default behavior for a new child company is to inherit from its parent company.
Password and MFA Options
If the parent company’s policy is not inherited, choose whether or not Password accounts (Mako CMS accounts without SSO) are allowed for users of the selected company.
If Password accounts are allowed, choose whether or not MFA is required for users of the selected company.
See the MFA description at the top of the page before choosing.
SSO Configuration
If the parent company’s policy is not inherited, choose whether or not SSO accounts are allowed for users of the selected company.
See the SSO description at the top of the page before choosing.
If you enable SSO, you should also configure at least one IdP below.
Save Button
Click the “Save” button to save these settings and apply them to relevant companies and users.
Behavior Summary
| Inherit Policy | Password | MFA Required | SSO Enabled | Behavior |
|---|---|---|---|---|
| Inherit policy from parent company | ||||
| Password required (MFA optional) SSO not allowed |
||||
| Password required (MFA required) SSO not allowed |
||||
| Password optional (MFA optional) SSO optional (MFA via IdP) |
||||
| Password optional (MFA required) SSO optional (MFA via IdP) |
||||
| Password not allowed SSO required (MFA via IdP) |
SSO Providers
SSO Providers List
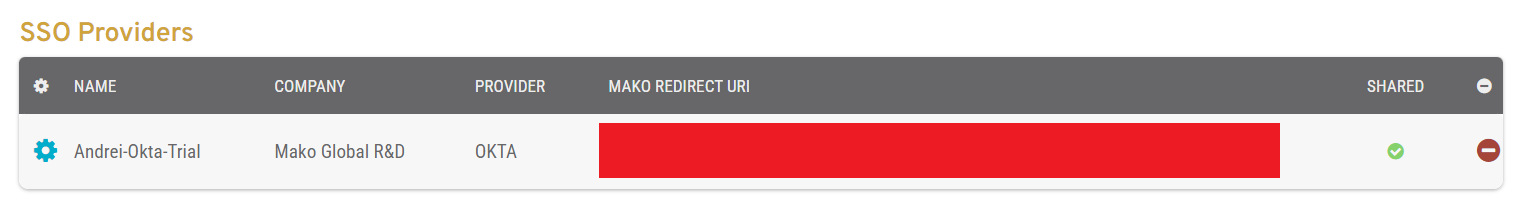
Figure 3. Example SSO Providers List
View the selected company’s currently configured SSO provider profiles in the SSO Providers list (Fig. 3).
Each provider profile registered in the Mako CMS is related to an app profile registered in a third-party IdP manager. The integration of these systems relies on the values in each system’s profile being the values expected by the other system.
Management of related profiles in both the Mako CMS and the appropriate IdP manager must be coordinated carefully.
See the Configuring SSO Integration guides for details regarding this process.
Columns
- [EDIT] – edit provider profile button
- NAME – name of provider profile (app profile from IdP)
- COMPANY – name of company that added provider profile
- PROVIDER – name of IdP
- MAKO REDIRECT URI – URI generated when provider profile was added; must be added to app profile in IdP
- SHARED – whether the provider profile is shared with customers (child companies)
- [DELETE] – delete provider profile button
Actions
Edit Provider Profile
To edit a provider profile, click its gear icon button. This will open the Edit SSO Provider form. Make and save any desired changes.
Management of related profiles in both the Mako CMS and the appropriate IdP manager must be coordinated carefully.
See the Configuring SSO Integration guides for details regarding this process.
Delete Provider Profile
To delete a provider profile, click its minus icon button. If you are certain you want to continue, click the “OK” button in the confirmation panel. Exercise caution, as this will affect any companies and users with access to this provider profile.
This will force affected users to choose a new authentication method the next time they log in.
See the Reset Password documentation for details regarding this process.
Add a New SSO Provider
Add a New SSO Provider Form
Figure 4. Example Add a New SSO Provider Form
Use the Add a New SSO Provider form (Fig. 4) to begin the process of adding a new provider profile.
Management of related profiles in both the Mako CMS and the appropriate IdP manager must be coordinated carefully.
See the Configuring SSO Integration guides for details regarding this process.
Form Fields
SSO Mode
Choose one of the available IdP integrations.
Add Provider Button
Click the “Add Provider” button to go to the next form.
Add SSO Provider Form
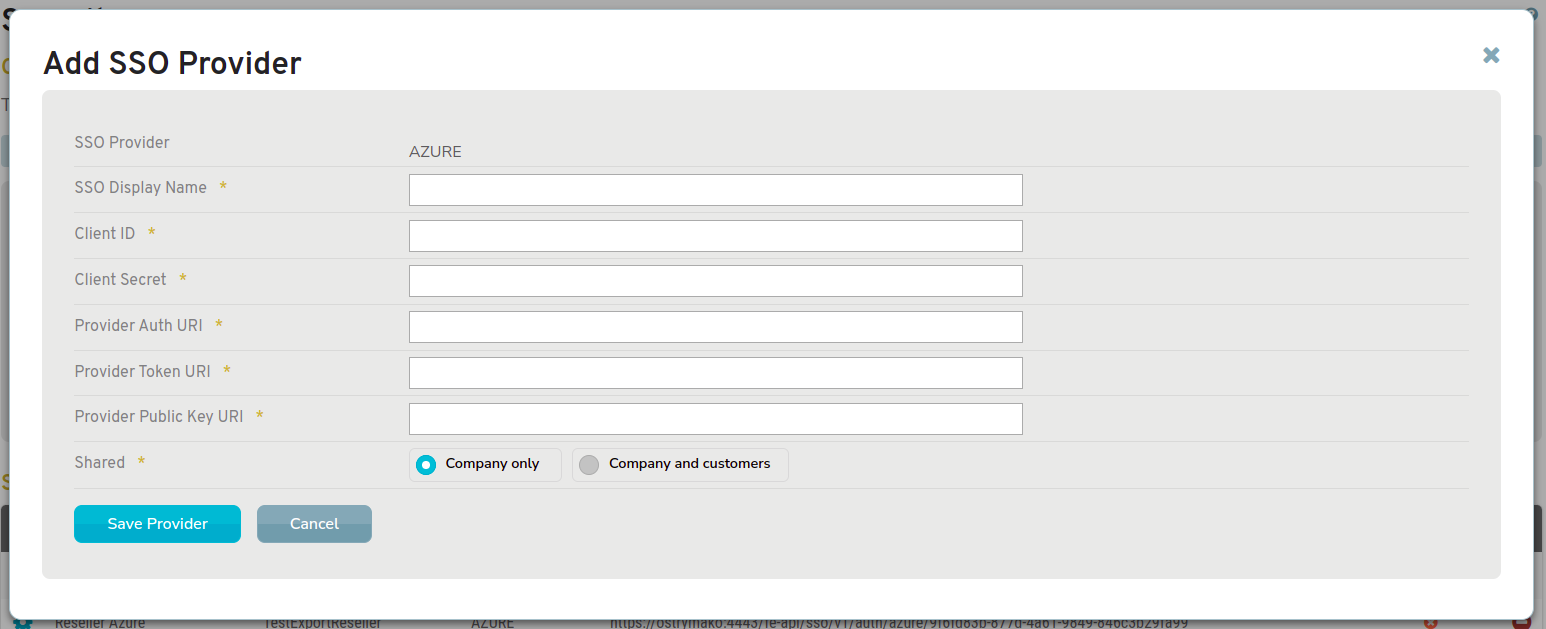
Figure 5. Example Add SSO Provider Form
Use the Add SSO Provider form (Fig. 5) to complete the process of adding a new provider profile.
Form Fields
SSO Provider
The IdP selected in the previous step is displayed.
SSO Display Name
Enter the name from the app profile in the IdP manager.
Client ID
Enter the client ID from the app profile in the IdP manager.
Client Secret
Enter the secret from the app profile in the IdP manager.
Provider Auth URI
Enter the authentication URI provided by the IdP.
Provider Token URI
Enter the token URI provided by the IdP.
Provider Public Key URI
Enter the key URI provided by the IdP.
Shared
Choose whether or not to make this provider profile available to child companies (customers) of the selected company.
Save Provider Button
Click the “Save Provider” button to create a new provider profile with these settings for the selected company.
Password Reset
Password Reset Form
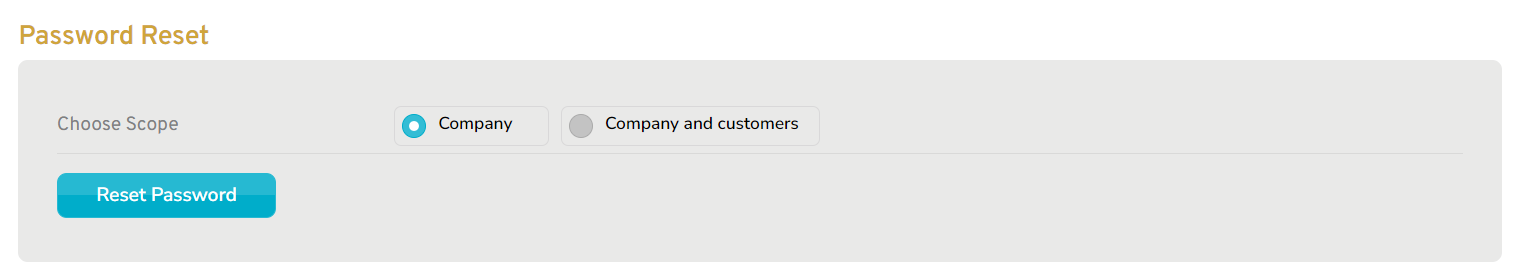
Figure 6. Example Password Reset Form
The Password Reset form (Fig. 6) allows you to reset the authentication method in bulk for users of the selected company. For users without SSO, resetting their authentication method resets their password.
This will force all users of the selected company to choose a new authentication method the next time they log in, regardless of their current authentication method (with or without SSO).
See the Reset Password documentation for details regarding this process.
Form Fields
Choose Scope
Choose whether or not to include the users of child companies (customers) of the selected company when resetting passwords.
Reset Password Button
Click the “Reset Password” button to open the Confirm Company Password Reset form.
Confirm Company Password Reset Form
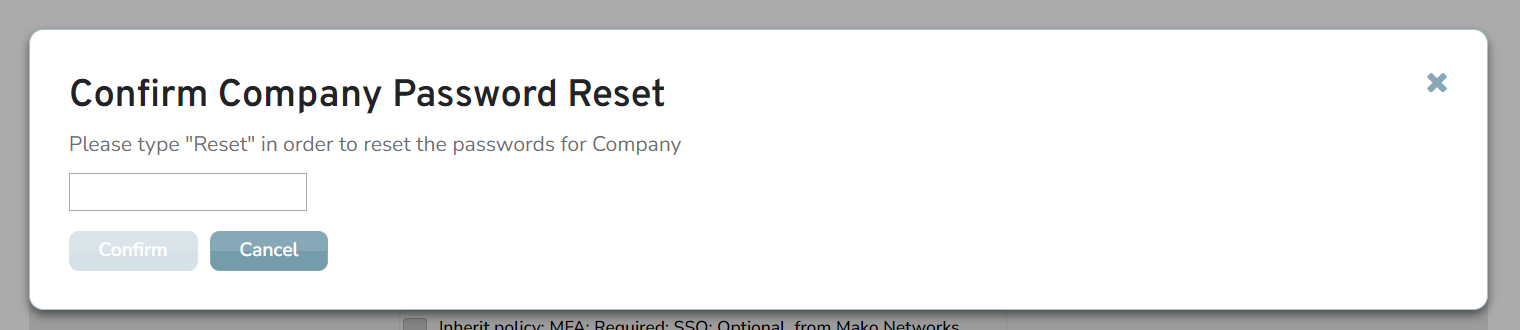
Figure 7. Example Confirm Company Password Reset Form
Use the Confirm Company Password Reset form (Fig. 7) to confirm this action.
Form Fields
Text
Enter “Reset” (case-insensitive) in the text field.
Confirm Button
Click the “Confirm” button to initiate the password reset process for relevant users.
