This topic is ONLY relevant to security gateways. It is NOT relevant to managed switches.
Overview
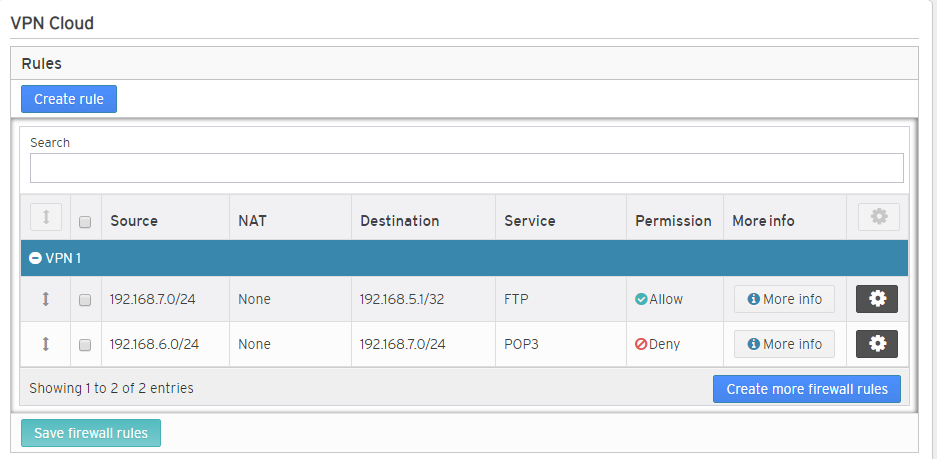
Figure 1. Example VPN Cloud Rules Page
The VPN Cloud Rules page (Fig. 1) allows you to manage firewall rules for the selected Mako that affect traffic for each Virtual Private Network (VPN) cloud.
If no custom rules have been created, the default rules will be used. The default rule for each VPN cloud allows all traffic.
Firewall rules are implemented from top to bottom as they appear on this page.
Create New Rule
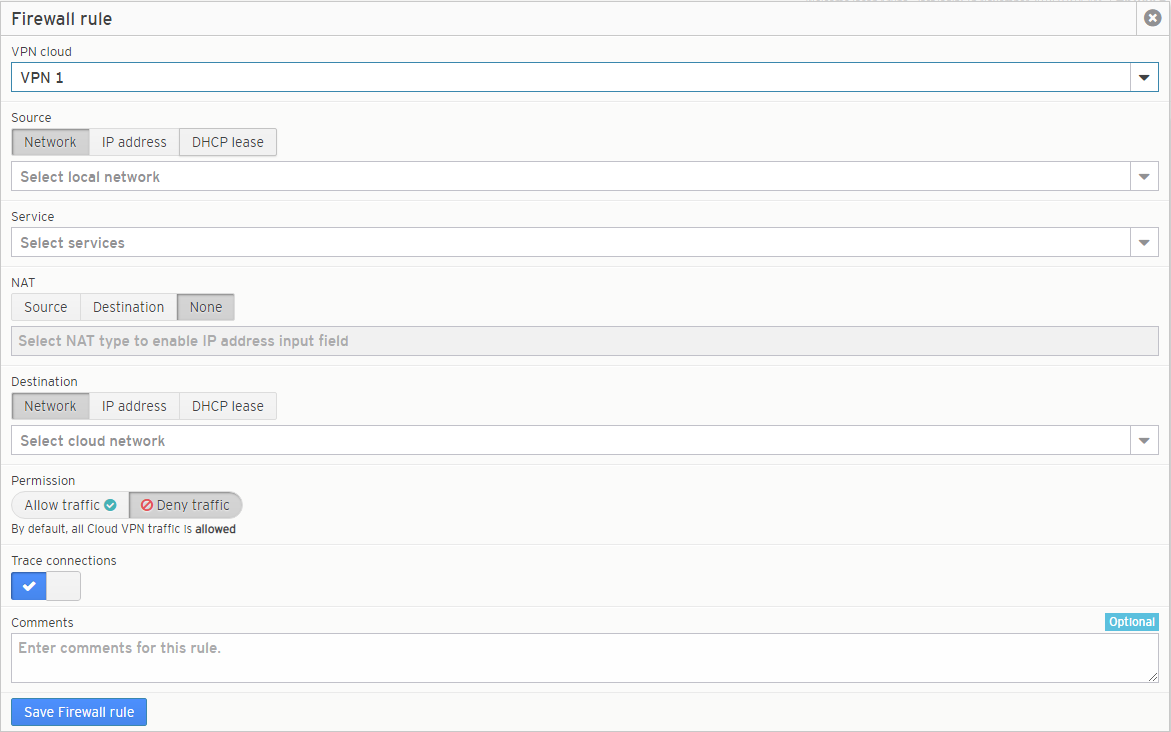
Figure 2. Firewall Rule Form with VPN Cloud Selected
To create a new VPN cloud firewall rule click either the “Create Rule” button or the “Create More Firewall Rules” button to open the Firewall Rule form (Fig. 2).
VPN Cloud
Choose the VPN cloud to which the firewall rule will apply. You can apply firewall rules to any VPN cloud associated with the selected Mako. After you select a VPN cloud, the other fields will become available.
Source
There are three methods for specifying the source of the VPN cloud traffic to which the new rule will apply. Click the appropriate tab for the method that you want to use.
Network
Choose a network from a list of registered networks. The selector includes a search field that will filter the list as you type.
IP Address
Enter the IP address and network mask (in CIDR notation). This can be a single device or an entire network.
DHCP Lease
Choose a device from a list of registered DHCP leases. The selector includes a search field that will filter the list as you type.
Service
Use the service type selector to specify the service type of the VPN cloud traffic to which the new rule will apply. The selector includes a search field that will filter the list as you type.
NAT
The “None” tab is selected by default. If your source or destination uses Network Address Translation (NAT), click either the “Source” tab or the “Destination” tab and enter the NAT IP address.
Destination
There are three methods for specifying the destination of the VPN cloud traffic to which the new rule will apply. Click the appropriate tab for the method that you want to use.
Network
Choose a network from a list of registered networks. The selector includes a search field that will filter the list as you type.
IP Address
Enter the IP address and network mask (in CIDR notation). This can be a single device or an entire network.
DHCP Lease
Choose a device from a list of registered DHCP leases. The selector includes a search field that will filter the list as you type.
Permission
Choose whether to allow or deny the VPN cloud traffic to which the new rule will apply. This is set to “Deny traffic” by default. Click the “Allow traffic” button to allow the traffic instead.
Trace Logging
Trace logging allows you to trace individual IP connections allowed and denied through the firewall. The trace information can be viewed on the Reports >> Syslogs page by selecting the “Firewall Logs” type. Trace logging is enabled by default. To disable it, click the blue checkmark button. Trace logging can negatively impact performance and should only be enabled while troubleshooting firewall-related connection problems. Trace logging is disabled automatically after four days.
Comments
Enter any additional comments you may have regarding this rule. These comments are restricted to a maximum of 64 characters.
Save Button
To create the new VPN firewall rule, click the “Save Firewall Rule” button.
View Existing Rules
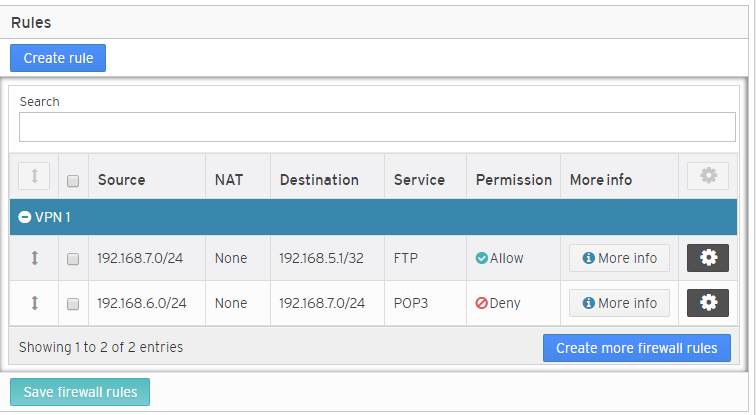
Figure 3. Example Existing Rules List
The Existing Rules list (Fig. 3) is where you can manage existing VPN cloud firewall rules. Rules in this list are grouped by VPN cloud.
Columns
- [Sort] – drag and drop handle for changing the rule’s priority (click and hold to drag; release to drop)
- [Select] – checkbox for selecting the rule (checkbox in column heading selects all rules)
- Source – source IP address and network mask to which the rule applies
- NAT – NAT IP address for either the source or destination
- Destination – destination IP address and network mask to which the rule applies
- Service – service type to which the rule applies
- Permission – whether the rule allows or denies traffic
- More Info – click to see comments and whether or not tracing is enabled
- [Options] – click to see edit and delete buttons
Edit Rule
To delete a VPN cloud firewall rule, click its gear icon button in the Options column. Then, click the “Edit” button. This will open the Firewall Rule form (Fig. 2).
Make any desired changes, then click the “Save Firewall Rule” button.
Change Rule Priority
To change the priority of a VPN cloud firewall rule within its VPN cloud list group, use the drag and drop handle in the Sort column. Click and hold the handle to drag the rule to a new position in the list group, then release the handle to drop the rule there.
Firewall rules are implemented from top to bottom of the list group. A good strategy for creating rules here is to create a “deny all traffic” rule first, and then add any exceptions to this rule as rules positioned below it.
Delete Rule
To delete a VPN cloud firewall rule, click its gear icon button in the Options column. Then, click the “Remove” button.
Alternatively, you can use the checkboxes in the Select column to specify a set of rules to delete. The checkbox in the column heading selects all rules. After you have checked at least one checkbox, the “Delete Selected Firewall Rules” button will become available. Then, click the “Delete Selected Firewall Rules” button.
Save Rules
New rules and rule changes made on this page are not implemented automatically. After you have created, edited, changed priority of, or deleted any rules on this page, you must click the “Save Firewall Rules” button to implement your changes or they will be lost.
