This topic is ONLY relevant to security gateways. It is NOT relevant to managed switches.
Overview
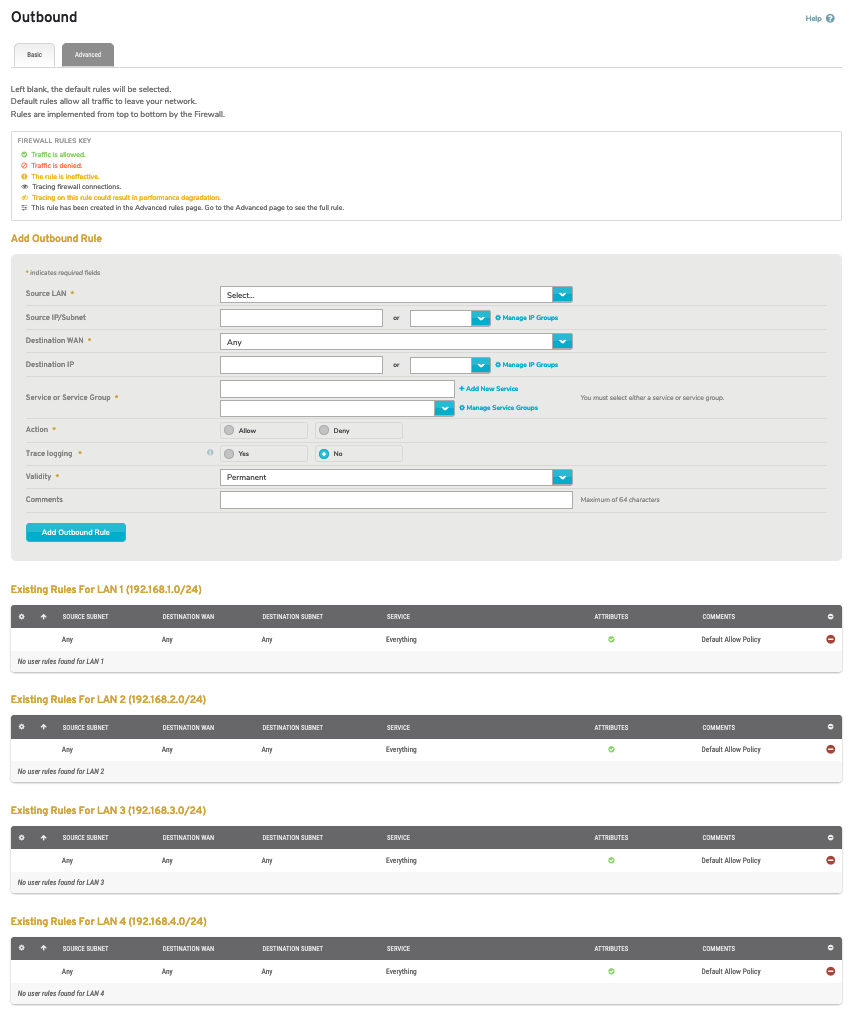
Figure 1. Example Outbound Rules Page
The Outbound Rules page (Fig. 1) allows you to manage firewall rules for the selected Mako that affect traffic outbound to each wide area network (WAN). You can create both basic and advanced firewall rules.
If no custom rules have been created, the default rules will be used. The default rules allow all outbound traffic to exit your network.
Firewall rules are implemented from top to bottom as they appear on this page.
Basic Settings
Use the Basic Settings tab (Fig. 1) to manage basic outbound firewall rules. If you need more control over the handling of outbound traffic than is provided here, you can use the Advanced Settings tab instead.
Add Outbound Rule
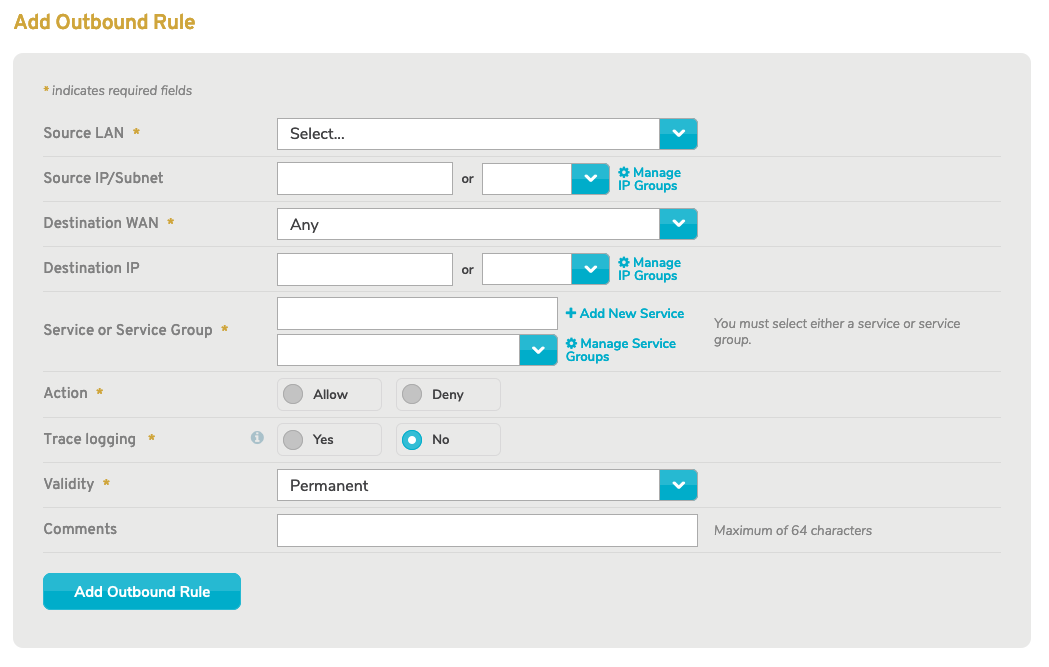
Figure 2. Example Add Outbound Rule Form
Use the Add Outbound Rule form (Fig. 2) to add a new outbound firewall rule.
Source IP Address
Enter the internal IP address and network mask (in CIDR notation) that is the source of the outbound traffic to which the new rule will apply. This can be a single device or an entire LAN.
Alternatively, use the Select a Network dropdown to choose the entire LAN that is the source of the outbound traffic to which the new rule will apply, or choose “All networks” if you want the new rule to apply to outbound traffic from all LANs.
Destination WAN
Choose the WAN that is the destination of the outbound traffic to which the new rule will apply, or choose “Any” if you want the new rule to apply to outbound traffic to all WANs.
Destination IP Address
Enter the external IP address and network mask (in CIDR notation) for the destination of the outbound traffic to which the new rule will apply, if you need to be more specific than choosing an entire destination WAN. Leave this blank if the new rule will apply to all IP addresses of the destination WAN.
Destination Domain
If you have enabled domain-based firewall rules in Services >> Advanced Settings, you can enter a domain value in the Destination IP Address field.
Domain-based firewall rules match the domain and all subdomains, e.g. “example.com” will match both example.com and www.example.com. The rule will also match all IP addresses that resolve to the specified domain and its subdomains.
Domain-based firewall rules require that clients use the Mako’s built-in DNS service. You can force all clients on a LAN to use the Mako’s DNS service by enabling the DNS Intercept option for the LAN.
WARNING: Domain-based firewall rules should only be used where the DNS server is secured from tampering, otherwise there is a risk of an intercepted DNS query providing the wrong IP information for the domain, resulting in the firewall rule allowing access to an unintended destination.
Service Type
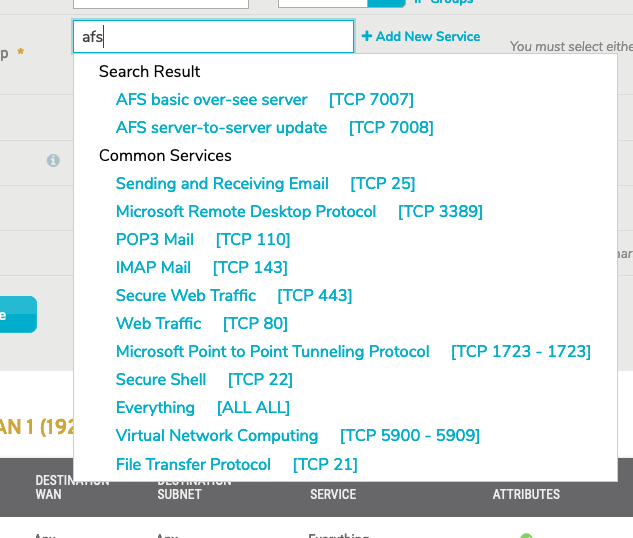
Figure 3. Example Service Type Selector
Use the service type selector (Fig. 3) to specify the service type of the outbound traffic to which the new rule will apply. The service type selector will display a Search Results list as you type. Below the Search Results list, you will see lists of Recent Services (if any have been selected recently) and Common Services. If the desired service type is visible in one of these lists, click the service type to select it. Otherwise, click the “Add new service” link below the selector to open the Add Service page (Fig. 4) in a new window.
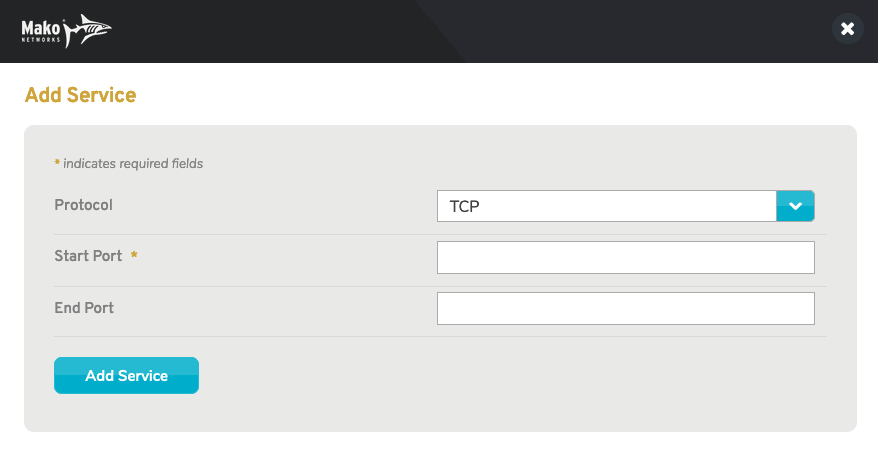
Figure 4. Example Add Service Page
Use the Add Service form (Fig. 4) to add a new service type by choosing a Protocol (either “TCP” or “UDP”), entering Start Port and End Port values, and then clicking the “Add Service” button.
Action
Choose whether to allow or deny the outbound traffic to which the new rule will apply. This is set to “Deny” by default. Click the “Allow” radio button to allow the traffic instead.
Comments
Enter any additional comments you may have regarding this rule. These comments are restricted to a maximum of 64 characters.
Add Button
To create the new outbound firewall rule, click the “Add” button.
Existing Outbound Rules
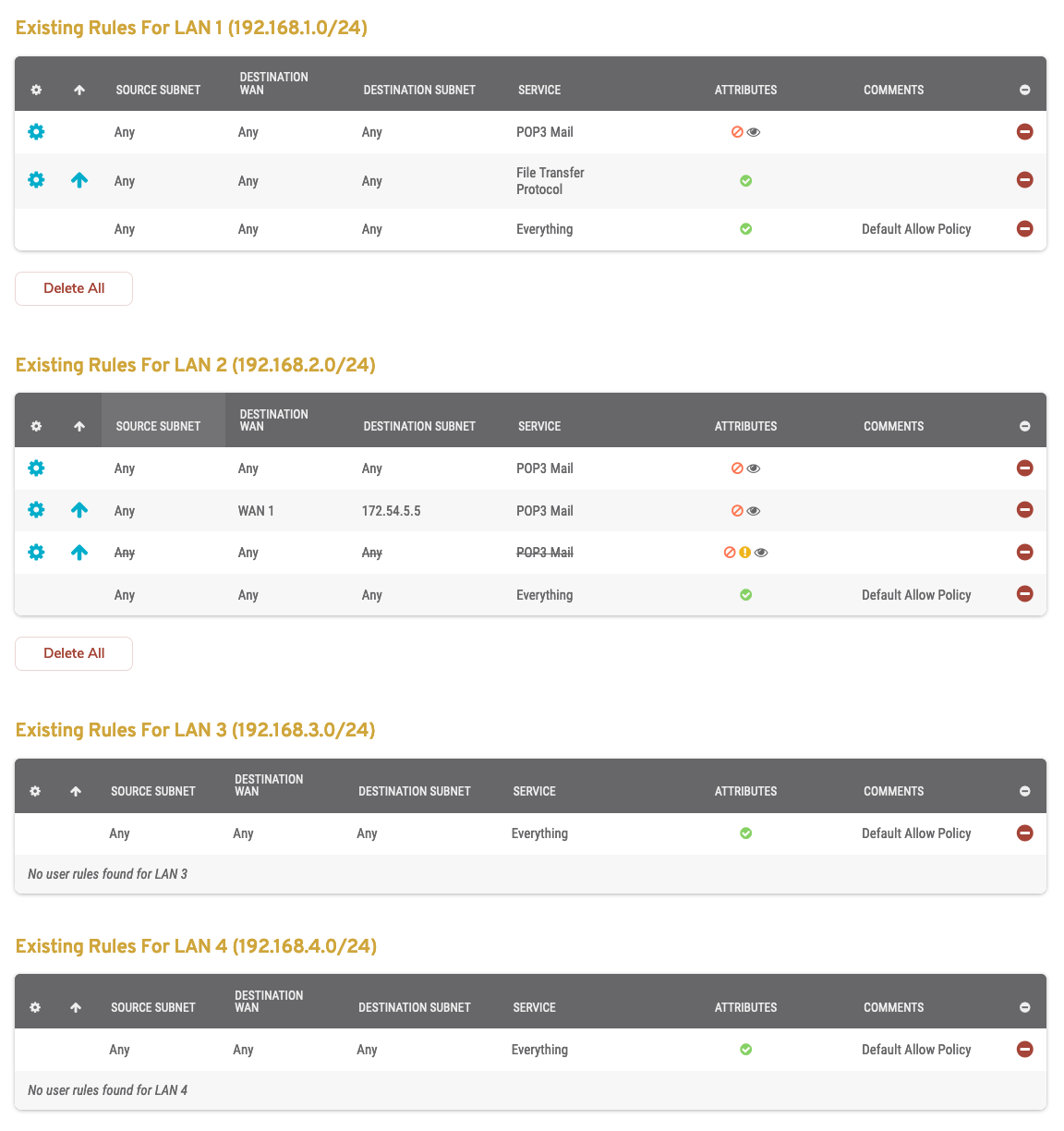
Figure 5. Example Existing Outbound Rules List
The Existing Outbound Rules list (Fig. 5) is where you can manage existing outbound firewall rules. Rules are grouped by Source IP Address in this list.
- WAN – destination WAN to which the rule applies
- Destination – external IP address and network mask or domain to which the rule applies
- Service – service type to which the rule applies
- Attributes – icons indicating whether the rule is allowing or denying traffic, whether or not the rule is an advanced rule, whether or not the rule is ineffective, whether or not tracing is enabled, and whether or not tracing could degrade performance
- Comments – comments describing the rule
- Options – edit, delete, and raise priority buttons
Edit Outbound Rule
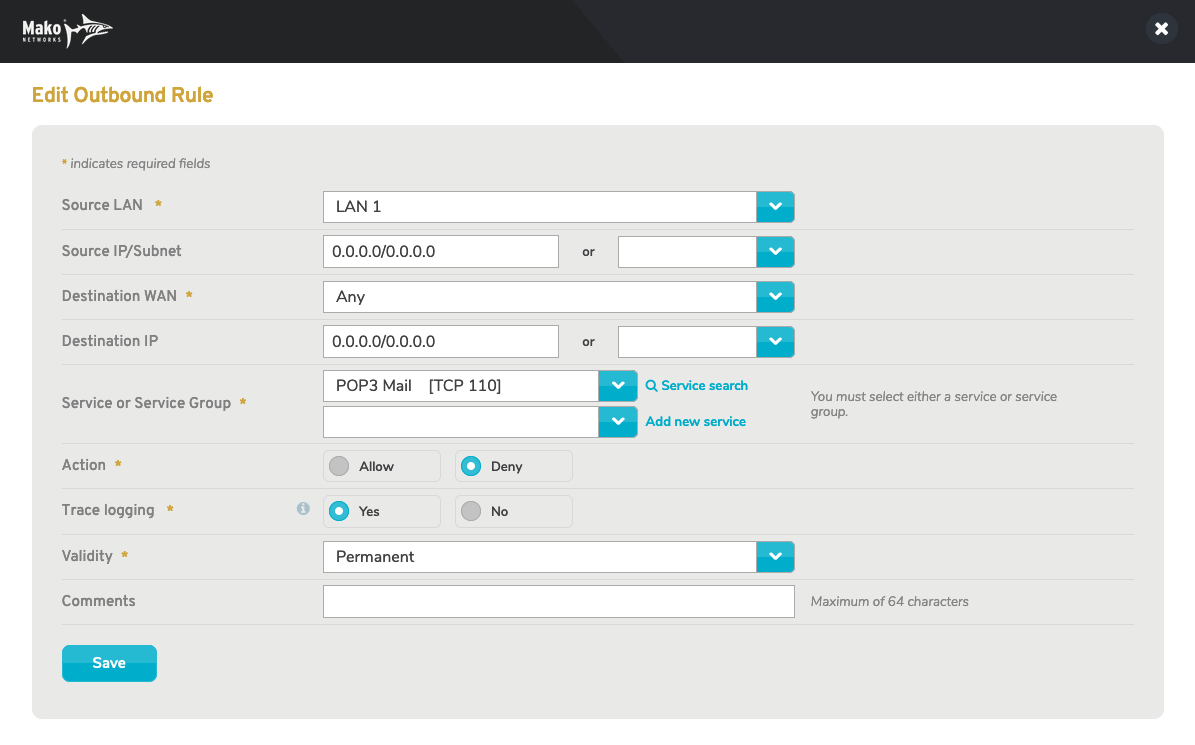
Figure 6. Example Edit Outbound Rule Form
To edit a firewall rule, click its gear icon button in the Options column. This will open the Edit Outbound Rule form (Fig. 6) in a new window.
See the advanced Add Outbound Rule form below for a description of the Trace Logging field.
Make any desired changes, then click the “Save” button.
Raise Outbound Rule Priority
To raise an outbound firewall rule one position in its Source IP Address list group, click its up arrow icon button in the Options column.
Firewall rules are implemented from top to bottom of the list group. A good strategy for creating rules here is to create a “deny all traffic” rule first, and then add any exceptions to this rule as rules positioned below it.
Delete Outbound Rules
To delete an outbound firewall rule, click its “-” icon button in the Options column. This will open a confirmation panel asking you to confirm the deletion. If you are certain you want to delete the outbound firewall rule, click the “OK” button.
To delete ALL existing outbound firewall rules for a Source IP Address list group at the same time, click the “Delete All” button at the bottom of the Source IP Address list group. This will open a confirmation panel asking you to confirm the deletions. If you are certain you want to delete ALL existing outbound firewall rules in the Source IP Address list group, click the “OK” button. This will delete BOTH basic and advanced outbound firewall rules.
Advanced Settings
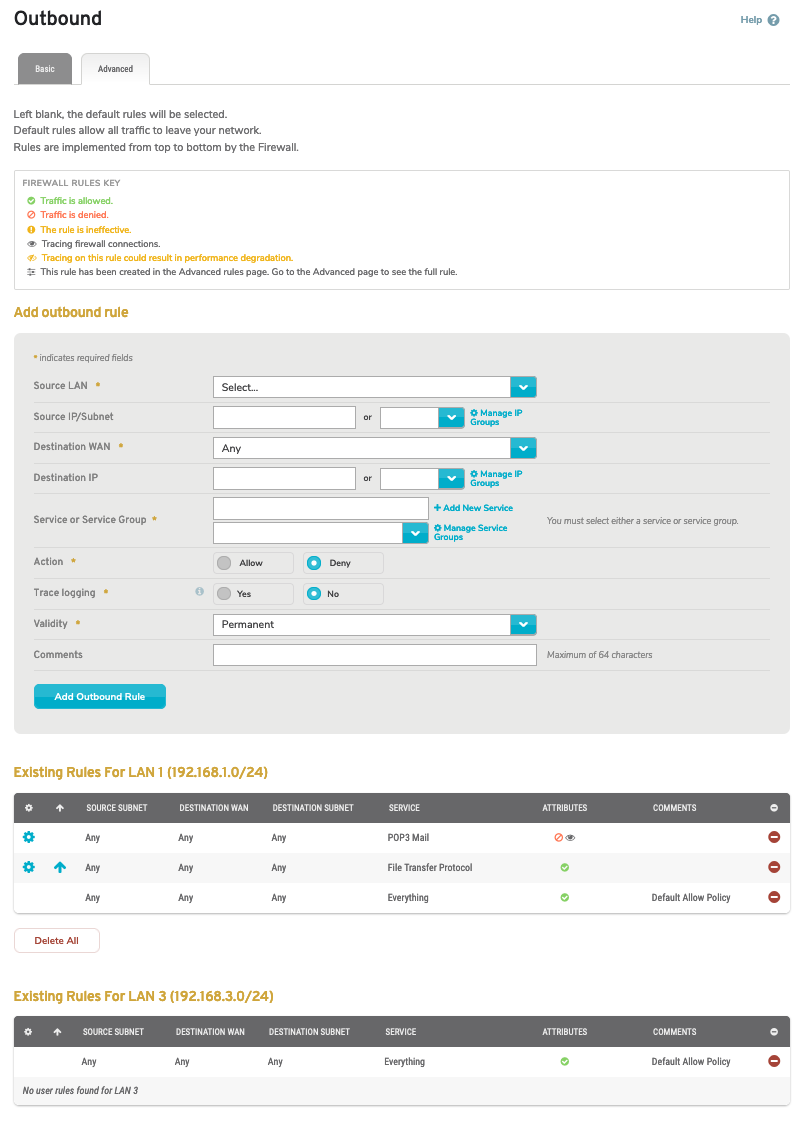
Figure 7. Example Advanced Settings Tab
Use the Advanced Settings tab (Fig. 7) to manage advanced outbound firewall rules.
Add Outbound Rule
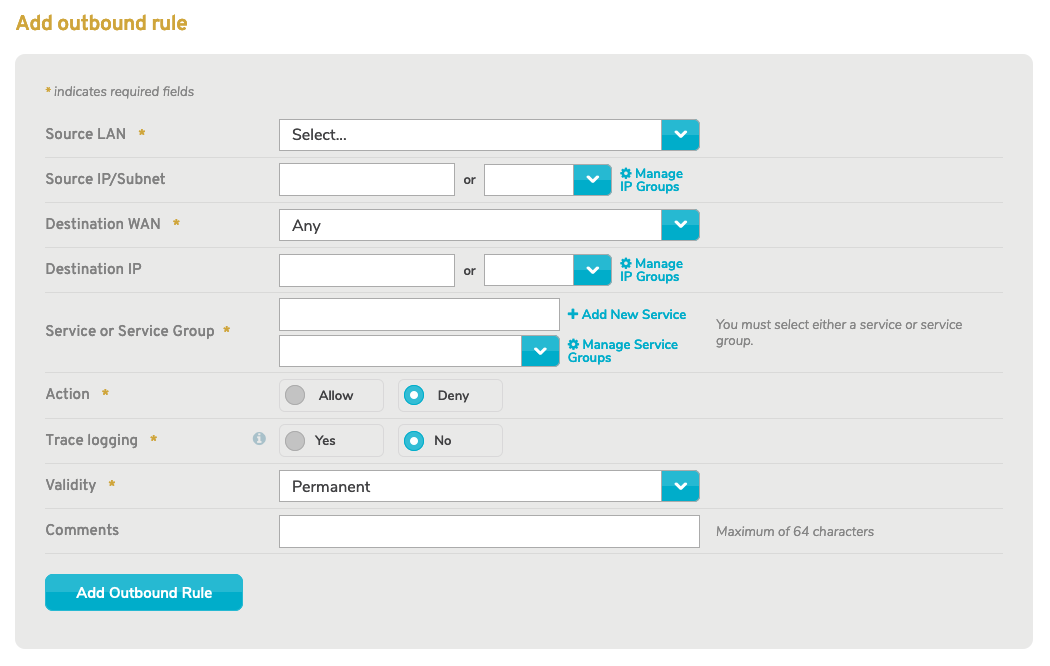
Figure 8. Example Advanced Add Outbound Rule Form
Use the advanced Add Outbound Rule form (Fig. 8) to add a new advanced outbound firewall rule.
Source IP Address/Mask
Enter the internal IP address and network mask (in CIDR notation) that is the source of the outbound traffic to which the new rule will apply. This can be a single device or an entire LAN.
As a convenience, you can click the “Network Mask” button to open a new window containing a list of network mask values, then click the desired value to populate Source IP Mask.
Destination WAN
Choose the WAN that is the destination of the outbound traffic to which the new rule will apply, or choose “Any” if you want the new rule to apply to outbound traffic to all WANs.
Destination IP Address/Mask
Enter the external IP address and network mask (in CIDR notation) for the destination of the outbound traffic to which the new rule will apply, if you need to be more specific than choosing an entire destination WAN. Leave this blank if the new rule will apply to all IP addresses of the destination WAN.
As a convenience, you can click the “Network Mask” button to open a new window containing a list of network mask values, then click the desired value to populate Destination IP Mask.
Destination Domain
If you have enabled domain-based firewall rules in Services >> Advanced Settings, you can enter a domain value in the Destination IP Address field.
Domain-based firewall rules match the domain and all subdomains, e.g. “example.com” will match both example.com and www.example.com. The rule will also match all IP addresses that resolve to the specified domain and its subdomains.
Domain-based firewall rules require that clients use the Mako’s built-in DNS service. You can force all clients on a LAN to use the Mako’s DNS service by enabling the DNS Intercept option for the LAN.
WARNING: Domain-based firewall rules should only be used where the DNS server is secured from tampering, otherwise there is a risk of an intercepted DNS query providing the wrong IP information for the domain, resulting in the firewall rule allowing access to an unintended destination.
Service Type
Use the service type selector to specify the service type of the outbound traffic to which the new rule will apply. The service type selector will filter its results as you type.
See the Service Type field in the basic Add Outbound Rule form for a full description of how to use the service type selector.
Action
Choose whether to allow or deny the outbound traffic to which the new rule will apply. This is set to “Deny” by default. Click the “Allow” radio button to allow the traffic instead.
Trace Logging
Trace logging allows you to trace individual IP connections allowed and denied through the firewall. The trace information can be viewed on the Reports >> Syslogs page by selecting the “Firewall Logs” type. Trace logging is disabled by default. To enable it, click the “Enable trace logging” checkbox. Trace logging can negatively impact performance and should only be enabled while troubleshooting firewall-related connection problems. Trace logging is disabled automatically after four days.
Comments
Enter any additional comments you may have regarding this rule. These comments are restricted to a maximum of 64 characters.
Add Button
To create the new outbound firewall rule, click the “Add” button.
Existing Outbound Rules
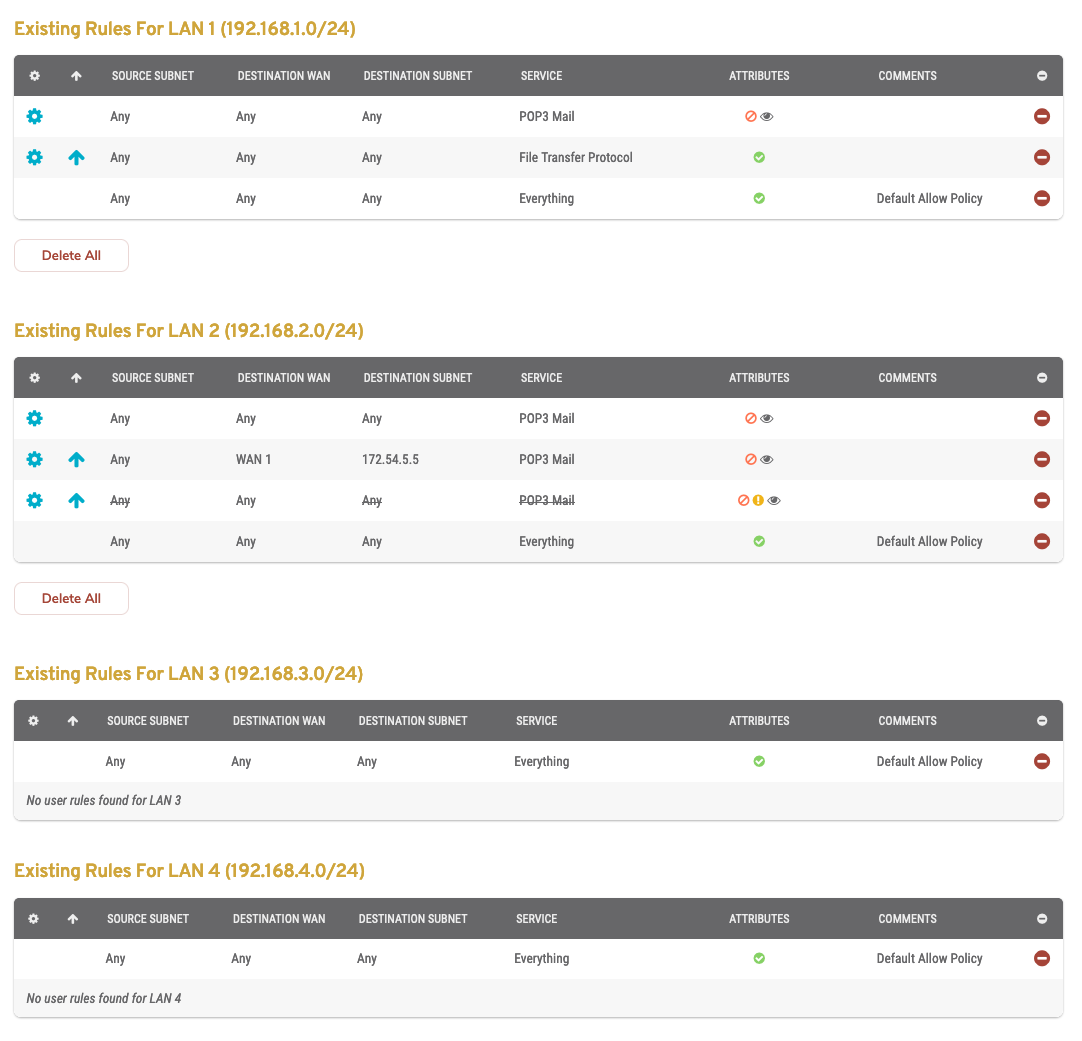
Figure 9. Example Advanced Existing Outbound Rules List
The advanced Existing Outbound Rules list (Fig. 9) is where you can manage existing advanced outbound firewall rules. Rules are grouped by Source IP Address in this list.
- Source – internal IP address and network mask to which the rule applies
- WAN – destination WAN to which the rule applies
- Destination – external IP address and network mask or domain to which the rule applies
- Service – service type to which the rule applies
- Attributes – icons indicating whether the rule is allowing or denying traffic, whether or not the rule is an advanced rule, whether or not the rule is ineffective, whether or not tracing is enabled, and whether or not tracing could degrade performance
- Comments – comments describing the rule
- Options – edit, delete, and raise priority buttons
Edit Outbound Rule
To edit an advanced firewall rule, click its gear icon button in the Options column. This will open the Edit Outbound Rule form (Fig. 6) in a new window.
Make any desired changes, then click the “Save” button.
Raise Outbound Rule Priority
To raise an outbound firewall rule one position in its Source IP Address list group, click its up arrow icon button in the Options column.
Firewall rules are implemented from top to bottom of the list group. A good strategy for creating rules here is to create a “deny all traffic” rule first, and then add any exceptions to this rule as rules positioned below it.
Delete Outbound Rules
To delete an outbound firewall rule, click its “-” icon button in the Options column. This will open a confirmation panel asking you to confirm the deletion. If you are certain you want to delete the outbound firewall rule, click the “OK” button.
To delete ALL existing outbound firewall rules for a Source IP Address list group at the same time, click the “Delete All” button at the bottom of the Source IP Address list group. This will open a confirmation panel asking you to confirm the deletions. If you are certain you want to delete ALL existing outbound firewall rules in the Source IP Address list group, click the “OK” button. This will delete BOTH basic and advanced outbound firewall rules.
