Overview
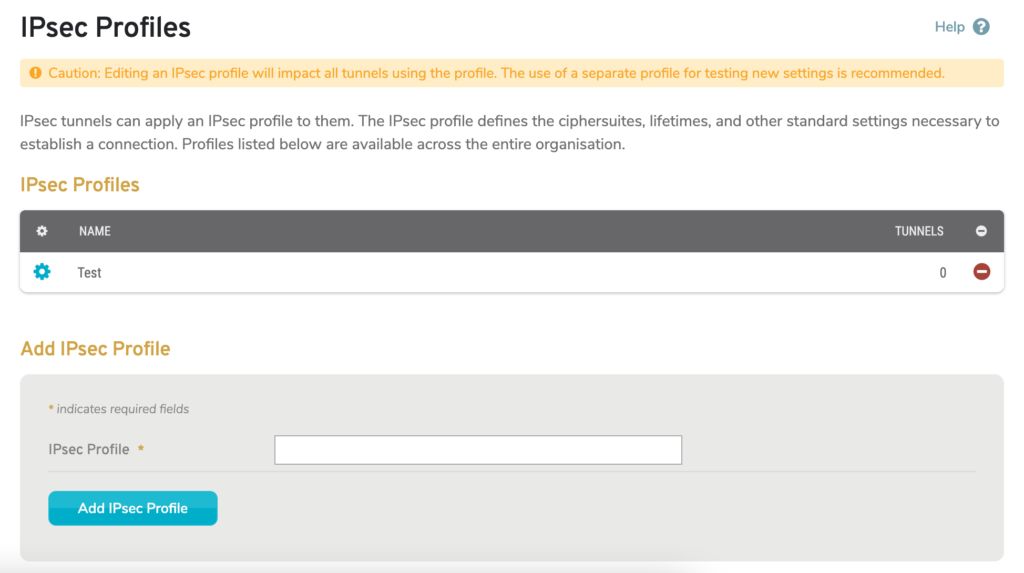
Figure 1. Example IPsec Profiles Page
The IPsec Profiles page (Fig. 1) allows you to manage IPsec Profiles for the selected company that can then be used when creating IPsec VPN tunnels. An IPsec Profile defines the ciphersuites, lifetimes, and other standard settings necessary to establish a connection.
Manage IPsec Profiles
Columns
- [Edit] – edit button
- Name – name of IPsec Profile
- Tunnels – number of VPN tunnels using IPsec Profile
- [Delete] – delete button
Actions
Edit IPsec Profile
To edit an IPsec Profile, click its gear icon button. This will open the Edit IPsec Profile form in a new window (Fig. 2). See below for details.
Delete IPsec Profile
To delete an IPsec Profile, click its minus icon button. This will open a confirmation panel asking you to confirm the deletion. If you are certain you want to delete the IPsec Profile, click the “OK” button. Exercise caution, as this will affect any VPN tunnels using this IPsec Profile.
Add New IPsec Profile
Enter a Name, then click the “Add IPsec Profile” button to create a new IPsec Profile.
After creating a new IPsec Profile, you will need to edit that profile in order to configure it for use. See below for details.
Edit Existing IPsec Profile
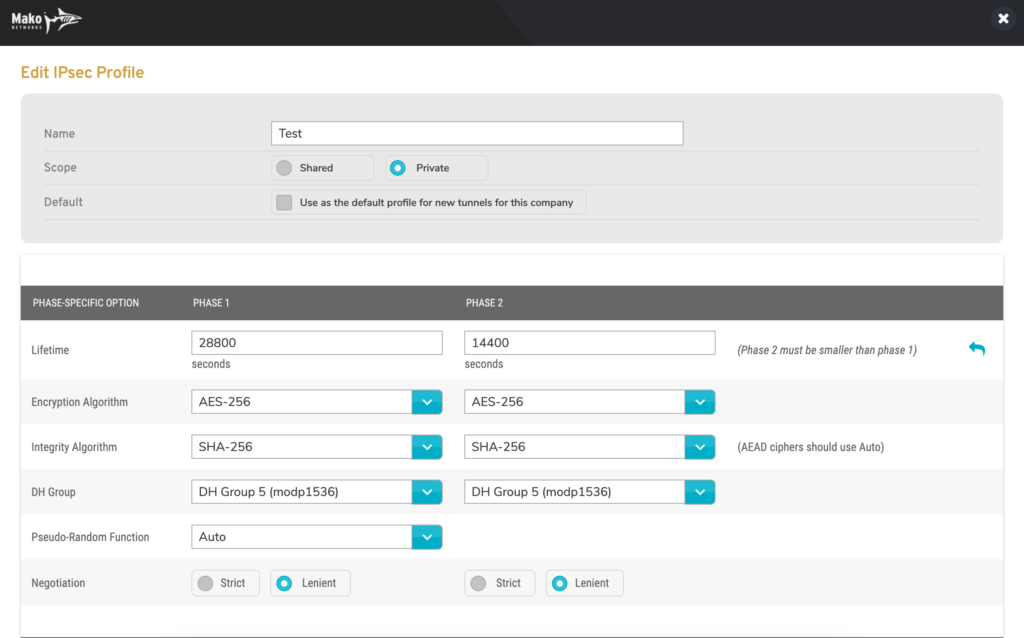
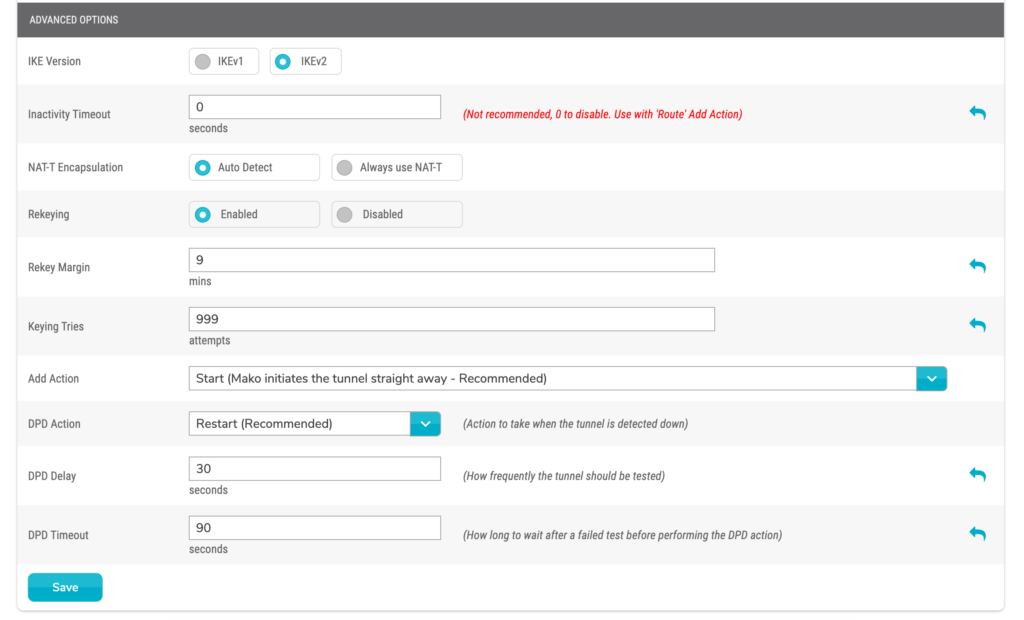
Figure 2. Example Edit IPsec Profile Page
Use the Edit IPsec Profile form (Fig. 2) to make any desired changes to this IPsec Profile, then click the “Save” button. Exercise caution, as this will affect any VPN tunnels using this IPsec Profile.
Some options in the form are only available for specific Mako device models. You may see a compatibility message below the form if there are any issues related to this.
Name
Enter an informative, memorable, and unique name for the Profile.
Scope
Choose whether this Profile is “Private” or “Shared.” Shared Profiles are available to child companies of this company.
Default
Check the checkbox to make this Profile the default Profile for new IPsec VPN tunnels for this company, if desired.
PHASE-SPECIFIC OPTIONS
Internet Key Exchange (IKE) is the protocol used to set up a security association (SA) in the IPsec protocol suite.
The IKE negotiation process has two phases. The settings grouped below can be configured independently for Phase 1 and Phase 2.
Lifetime
Enter the number of seconds you want the IPSec security association to live for both Phase 1 and Phase 2. The Phase 2 value must be smaller than the Phase 1 value.
You can click the “Use defaults” arrow icon in the rightmost column to reset these values to the default values.
Encryption Algorithm
Choose the algorithms to use to encrypt data for both Phase 1 and Phase 2.
Integrity Algorithm
Choose the algorithms to use to authenticate data integrity for both Phase 1 and Phase 2. AEAD ciphers should use the “Auto” option.
DH Group
Choose the Diffie-Hellman (DH) groups to use to determine shared secrets for both Phase 1 and Phase 2.
Pseudo-Random Function
Choose the Pseudo-Random Function (PRF) to use to provide randomness in cryptographic processes.
Negotiation
Choose either the “Strict” or “Lenient” negotiation mode for both Phase 1 and Phase 2. “Strict” negotiation is recommended to maintain compatibility with devices that do not allow “Lenient” negotiation.
ADVANCED OPTIONS
IKE Version
Choose the version of IKE to use. IKEv2 is NOT supported by the following Mako models: 6500, 6500-M, and 8875.
Inactivity Timeout
Enter the number of seconds of inactivity before timeout. It is recommended to use the default value of zero (0) seconds to disable this timeout; however, if you are using “Route” as the Add Action, you may need to change this value.
You can click the “Use defaults” arrow icon in the rightmost column to reset this value to the default value.
NAT-T Encapsulation
NAT Traversal (NAT-T) allows encapsulated traffic to use the VPN to reach the destination when the source does not have a unique public IP address.
Choose either the “Auto Detect” or “Always use NAT-T” option for this feature. It is recommended to use the “Always use NAT-T” option.
Rekeying
The Rekeying feature automatically initiates rekeying upon expiration of an existing key.
Choose either the “Enabled” or “Disabled” option for this feature.
Rekey Margin
Enter the number of minutes prior to SA expiration when rekeying should begin (if rekeying is enabled).
You can click the “Use defaults” arrow icon in the rightmost column to reset this value to the default value.
Keying Tries
Enter the number of attempts to make when rekeying (if rekeying is enabled).
You can click the “Use defaults” arrow icon in the rightmost column to reset this value to the default value.
Add Action
Choose how to handle Add action requests. The following options are available:
- Add (Other end must initiate the tunnel)
- Start (Mako initiates the tunnel straight away – Recommended)
- Route (Mako initiates the tunnel only when it sees traffic for it – Not Recommended)
- Ignore (Do not add the tunnel at all)
DPD Action
Dead Peer Detection (DPD) is a feature that can determine when a peer device is “dead” or unavailable.
Choose the action to take when the tunnel is detected down. The following options are available:
- None
- Clear (Stop and unroute all connections with dead peer)
- Hold (Put all connections with dead peer in a “suspended state”)
- Restart (Restart all connections with dead peer – Recommended)
DPD Delay
Enter the number of seconds to wait between each DPD keepalive check.
You can click the “Use defaults” arrow icon in the rightmost column to reset this value to the default value.
DPD Timeout
Enter the number of seconds between detecting a dead peer device and actually declaring the peer device dead, triggering the DPD Action. This value should be three times the DPD Delay in order to reduce the risk of false positives.
You can click the “Use defaults” arrow icon in the rightmost column to reset this value to the default value.
SAVE BUTTON
To save any changes made in the Edit IPsec Profile form, click the “Save” button.
