Overview
The Mako Central Management System (CMS) now supports Single Sign-On (SSO). With SSO, you can allow users to access the Mako CMS using third-party accounts created via an SSO identity provider (IdP).
For Mako CMS accounts without SSO, account credentials are managed via the Mako CMS. For Mako CMS accounts with SSO, account credentials are managed via the SSO identity provider.
This document guides you through the steps to configure SSO integration with Okta as the IdP. See below for guides to other currently supported IdPs.
Currently Supported IdPs
- Microsoft Entra ID (formerly Azure Active Directory)
- Okta
General IdP Configuration Process
- Step 1: Register App Profile in IdP Manager
- Step 2: Register Provider Profile in Mako CMS
- Step 3: Register Redirect URI in IdP Manager
For detailed information regarding your specific SSO identity provider, your account with them, and your use of their products and services, please refer to the identity provider’s documentation and support. Mako Support can assist you with this, but the identity provider should have the most up-to-date information.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) adds an extra layer of security to user accounts by requesting a new access code each time the user logs in. MFA is recommended for any user, but it is required for those maintaining PCI DSS compliance.
Companies that require PCI DSS compliance must enforce MFA for all users. For Mako CMS accounts without SSO, MFA is managed via the Mako CMS. For Mako CMS accounts with SSO, MFA is managed via the SSO identity provider.
Okta
Step 1: Register App Profile in IdP Manager
- Go to Okta’s Admin Dashboard: https://login.okta.com.
- Navigate to Applications > Applications.
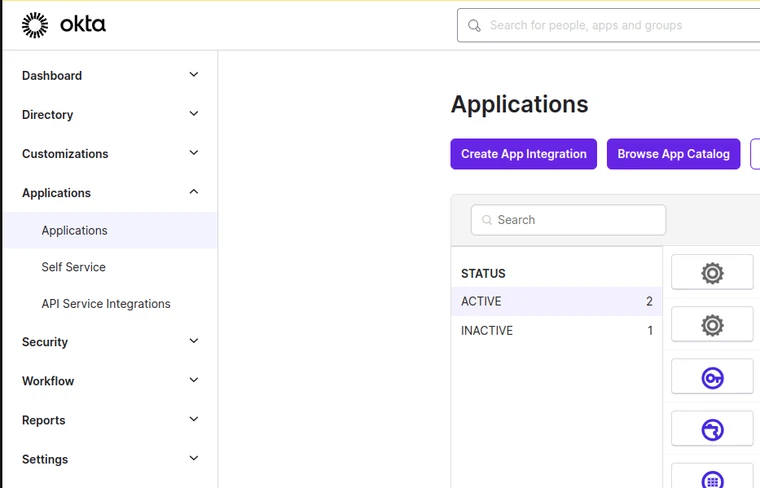
Figure 1. Example Okta Applications Page
- Click “Create App Integration” at the top of the Applications page (Fig. 1).
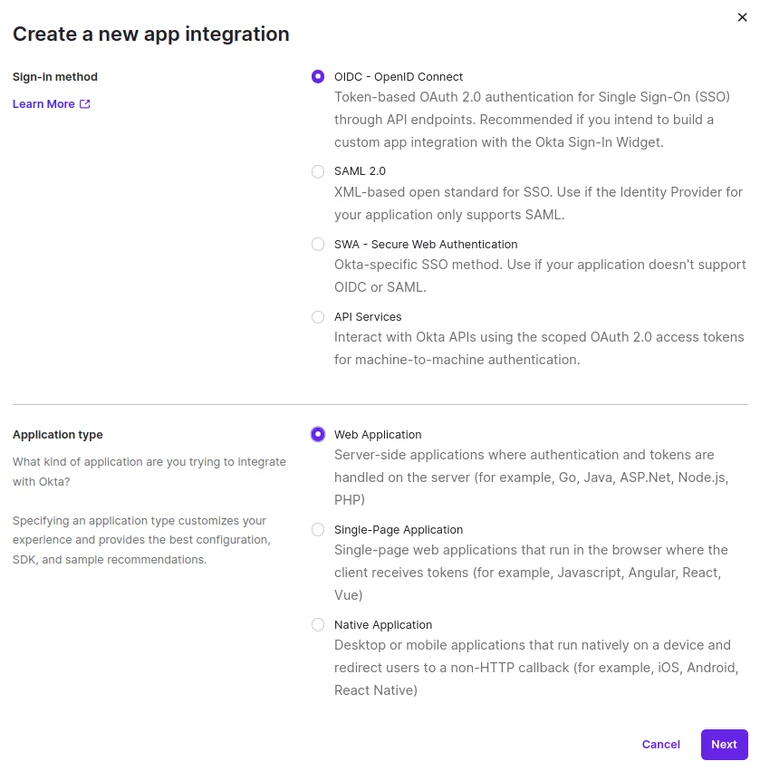
Figure 2. Example Okta Create a New App Integration Form
- Choose “OIDC – OpenID Connect” for Sign-in method in the Create a new app integration form (Fig. 2).
- Choose “Web Application” for Application type.
- Click the “Next” button.
- Enter the following values in the next form.
| App integration name | Enter an informative name, such as “Mako-Okta App”. You will need this in Step 2. |
|---|---|
| Grant type | Choose the “Authorization Code” option. |
| Sign-in redirect URIs | Leave this empty for now. You will update this in Step 3. |
| Sign-out redirect URIs | https://comp.makonetworks.com/ |
| Controlled access | Choose the appropriate access for your organization. (You can skip this for now and update it later, if necessary.) |
- Click the “Save” button to create a new app profile with these settings.
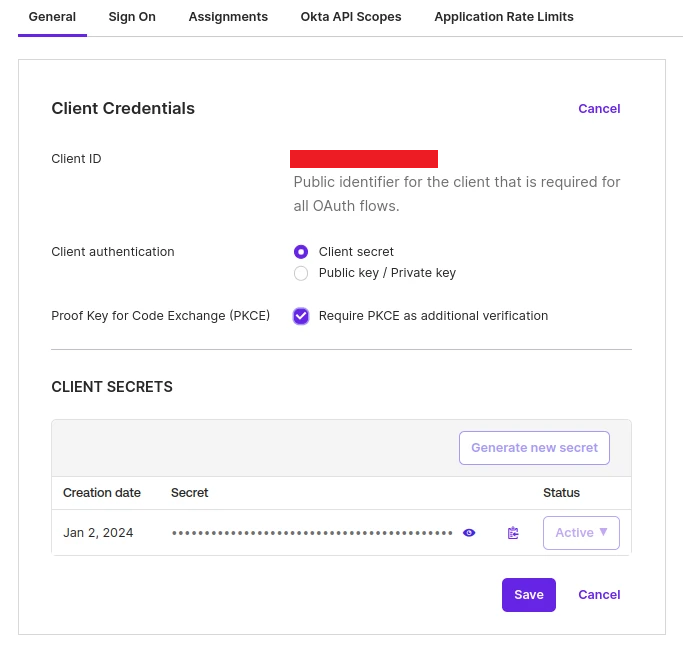
Figure 3. Example Okta App Profile Page
- Click the “Edit” button on the General tab of the App Profile page (Fig. 3).
- Copy and save the Client ID.
You will need this in Step 2. - Copy and save the Secret.
You will need this in Step 2. - Check the “Require PKCE as additional verification” checkbox.
- Click the “Save” button to save this change.
Step 2: Register Provider Profile in Mako CMS
- Go to the Mako CMS and select the appropriate company.
- Navigate to Companies > Manage Company > Security.
See the Company Security documentation for more details.
- In the Add a New SSO Provider form, choose “Okta” for SSO Mode, then click the “Add Provider” button.
- Enter the following values in the Add SSO Provider form.
| SSO Display Name | Enter the App integration name from Step 1. |
|---|---|
| Client ID | Enter the Client ID from Step 1. |
| Client Secret | Enter the Secret from Step 1. |
| Provider Auth URI | https://OKTA_ID.okta.com/oauth2/v1/authorize (Replace OKTA_ID with your Client ID.) |
| Provider Token URI | https://OKTA_ID.okta.com/oauth2/v1/token (Replace OKTA_ID with your Client ID.) |
| Provider Public Key URI | https://OKTA_ID.okta.com/oauth2/v1/keys (Replace OKTA_ID with your Client ID.) |
| Shared | Choose the appropriate option for this company. |
You should verify the URI values with your IdP. For example, the current version number may have changed after this document was created.
- Click the “Save Provider” button to create a new provider profile with these settings for the selected company.
- Copy and save your new provider’s Mako Redirect URI from the SSO Providers list.
You will need this in Step 3.
Step 3: Register Redirect URI in IdP Manager
- Return to the App Profile page in Okta’s Admin Dashboard.
- Click the Sign On tab, then click the “Edit” button.
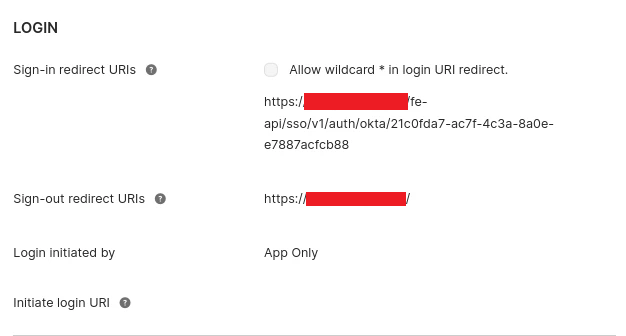
Figure 4. Example Okta Sign On Tab
- Enter the following value in the form (Fig. 4).
| Sign-in redirect URIs | Enter the Mako Redirect URI value from Step 2. |
|---|
- Click the “Save” button to save this change.
Next Steps
Congratulations! You have configured Okta as the SSO IdP for your selected company. You may want to configure additional IdPs for this company or configure IdPs for other companies that you manage.
To complete your SSO deployment, you must configure which Mako CMS companies and users are allowed to use SSO. See the following documentation for details.
