Overview
The Mako System provides IDS/IPS services based on Suricata.
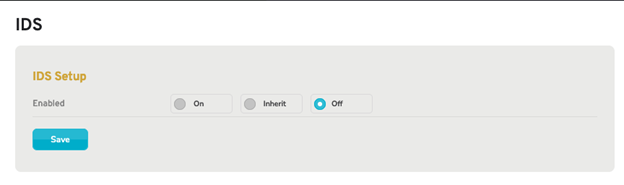
Figure 1. Example IDS Starting Page
The IDS Starting page (Fig. 1) allows you to enable intrusion detection and prevention systems (IDS/IPS) and further apply IDS profiles (sets of IDS rules) to the selected Mako security gateway. This service will either alert you when blacklisted traffic is detected (IDS mode) or automatically drop connections related to blacklisted traffic (IPS mode).
You have three options from which to choose: “On,” “Inherit,” and “Off.”
- Off – default, IDS/IPS disabled
- Inherit – IDS settings are set in a company Enterprise Template (ET) and are inherited at the device level from the ET. No changes to the settings are allowed at the device level. See the Enterprise Templates documentation for more information.
- On – IDS settings enabled but only apply to the current device.
IDS Setup Form
From the starting page, select ON unless you have preconfigured IDS settings in a company Enterprise Template. This will open the IDS Setup Page (Fig 2 below)
Enable IDS: On
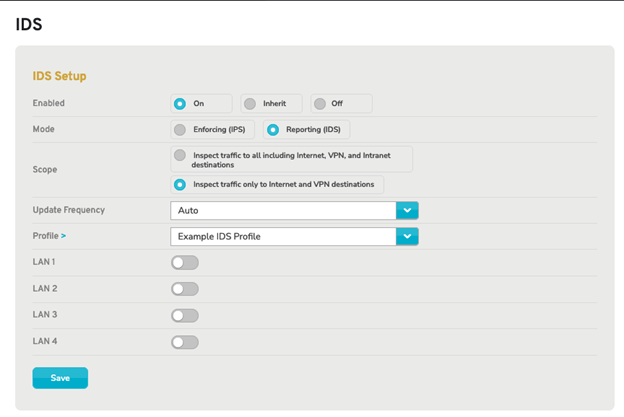
Figure 2. Enable IDS with “On” Selected
Use caution when enabling this feature, as it may impact performance.
Choosing the “On” option makes the following fields available:
Mode
Choose either “Enforcing (IPS)” or “Reporting (IDS)” mode for the IDS/IPS service. IDS mode will alert you when blacklisted traffic is detected without taking any further action. IPS mode will automatically drop connections related to blacklisted traffic.
Best practice is to start with Reporting/IDS mode until you have verified the configuration you want.
Scope
Choose the scope of traffic that the IDS/IPS service will inspect: either all traffic (including Internet, VPN, and Intranet destinations) or only traffic related to Internet and VPN destinations.
Update Frequency
Choose how often the IDS profile is updated and rebuilt with the latest IDS rules. This can be set from every hour to every week, depending on your needs.
LANs
Specify which LANs (including VLANs and WLANs) are monitored and/or protected by the IDS/IPS service. To enable IDS/IPS activity for a specific LAN, click the gray checkmark icon or the red stop sign icon. To disable IDS/IPS activity for a specific LAN, click the gray stop sign icon or the green checkmark icon.
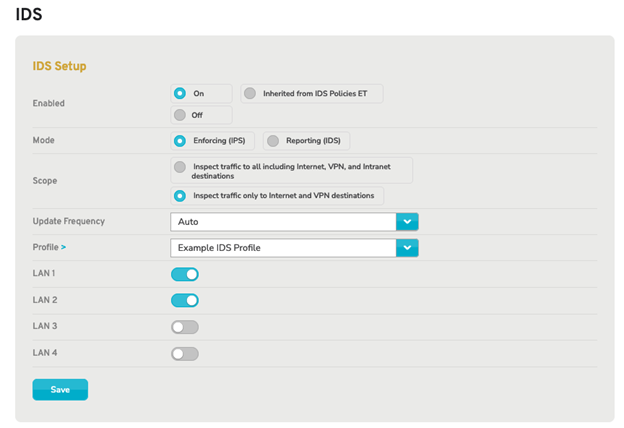
Figure 3. LANs 1 and 2 selected for IDS inspection
Profile
Choose the IDS profile that the IDS/IPS service will use to detect blacklisted traffic. If no IDS profiles are available, click the yellow arrow icon link next to the “Profile” label, to visit the IDS Select page and create a new IDS profile.
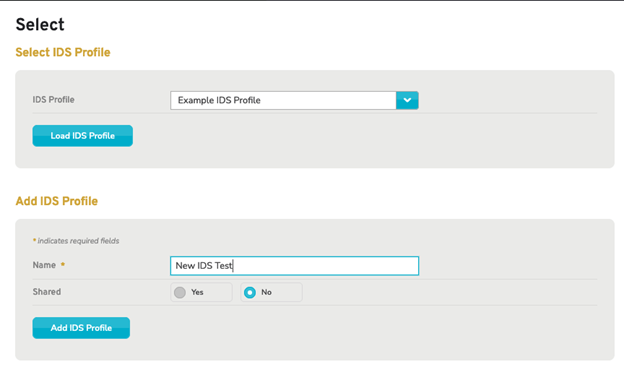
Figure 4. Select or Create IDS Profile
To create a new profile, provide a meaningful name and elect to share this profile with any company entities created under the parent or no to limit it to just the present company and click “Add IDS Profile”.
This will take you to the IDS Profile Setup page and confirmation that the new IDS profile was created.

Figure 5. IDS Profile Setup Page
Next, in the left menus, select Rules under IDS which will take you to the Rule Source Subscription page where you can elect to enable rule groups and set them to Auto, Alert, Drop or Pass.
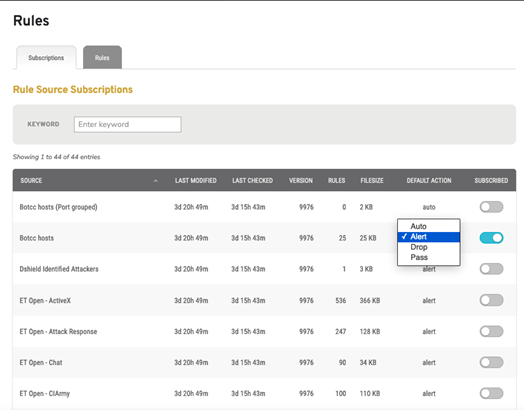
Figure 6. Mako Subscriptions List
Alternatively, you can scroll to the bottom of the page and elect to use the Mako recommended subscriptions.
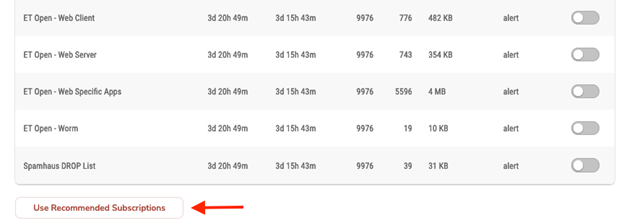
Figure 7. Mako Recommended Subscriptions Election
Best practice is to elect to use the Mako recommended subscriptions as a starting point unless you are well-versed in IDS/IPS. This election is suitable for most needs.
Enable IDS: Inherit
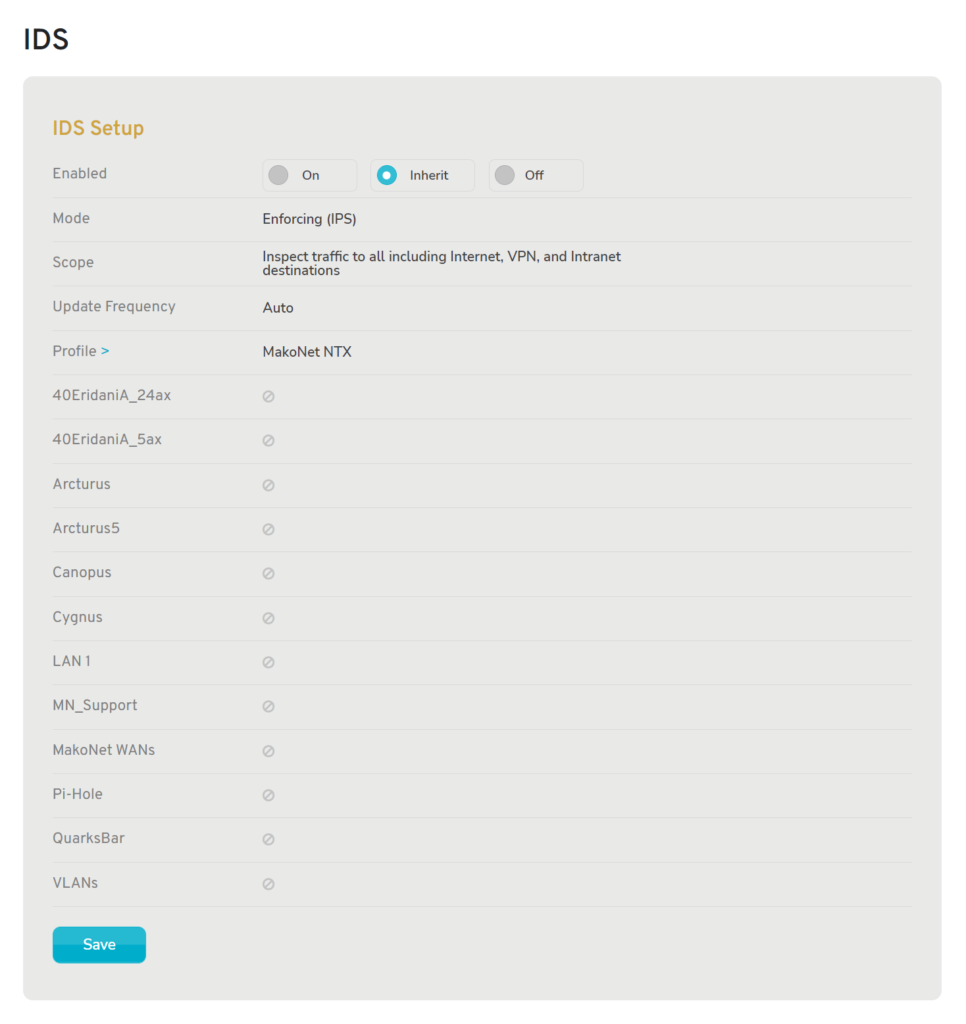
Figure 8. Enable IDS with “Inherit” Selected
Setting the IDS/IPS feature to the “Inherit” option (Fig. 3) will enable or disable the feature based on the Enterprise Template(s) applied to the selected Mako. If any Enterprise Template applied to the selected Mako has IDS/IPS enabled, then IDS/IPS will be enabled. Otherwise, it will be disabled.
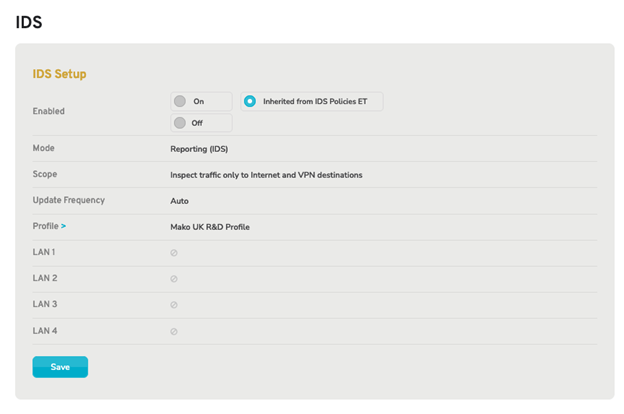
Figure 9. IDS Inherited from active Enterprise Template
Note that if the IDS settings are inherited, you cannot make any changes to the settings at the device level and would need to update the IDS settings in the relevant Enterprise Template (ET).
Enable IDS: Off

Figure 10. Enable IDS with “Off” Selected
To explicitly disable IDS/IPS for the selected Mako, choose the “Off” option, then click the “Save” button (Fig. 4). This is the default setting for the IDS/IPS feature.
Save Button
To save any changes you have made here, click the “Save” button.
